
How to Stay on Top of Cybersecurity News
The top tools and news sources you need to know if you are in cybersecurity. Don’t get caught off guard by an attack!

The top tools and news sources you need to know if you are in cybersecurity. Don’t get caught off guard by an attack!

How to audit and better secure Active Directory passwords. The latest updates to enterprise password policy and best practices. Tips on how you can stay up to date on breaches.

How you can create fun and engaging cybersecurity tabletop exercises at your organization. Fulfill compliance requirements for tabletop exercises or security awareness training with the provided documents.

If you are not using these free tools to secure Active Directory, then you’re an easy target! Find the vulnerabilities lurking in your Active Directory environment before the attackers do.

How to securely create a Windows Scheduled Task that requires high domain level privileges. Leveraging standalone Managed Service Accounts(sMSA) to automate administrative tasks.

Many Active Directory attacks’ root vulnerability is the domain’s AD Access Control Lists. This post explains what you need to know about the AD Access Control List to prevent lateral movement and escalation of privileges in the domain.

The tips you need to know for the Hack The Box Dante Pro Lab challenge. Are you ready for the challenge? My review of Hack The Box’s Dante Pro Lab.

Are you defending PowerShell abuse in your network? Find out the PowerShell best practices for preventing abuse.

Are you planning on attending DEF CON 33? Check out my guide if this will be your first DEF CON. The helpful tips you need to maximize your DEF CON 33 experience.

Are you planning on attending DEF CON 33? Check out my guide if this will be your first DEF CON. The helpful tips you need to maximize your DEF CON 33 experience.

A focused guide to the core password cracking tools every beginner should know—covering hash identification, cracking utilities, and more to help you crack smarter, not harder.
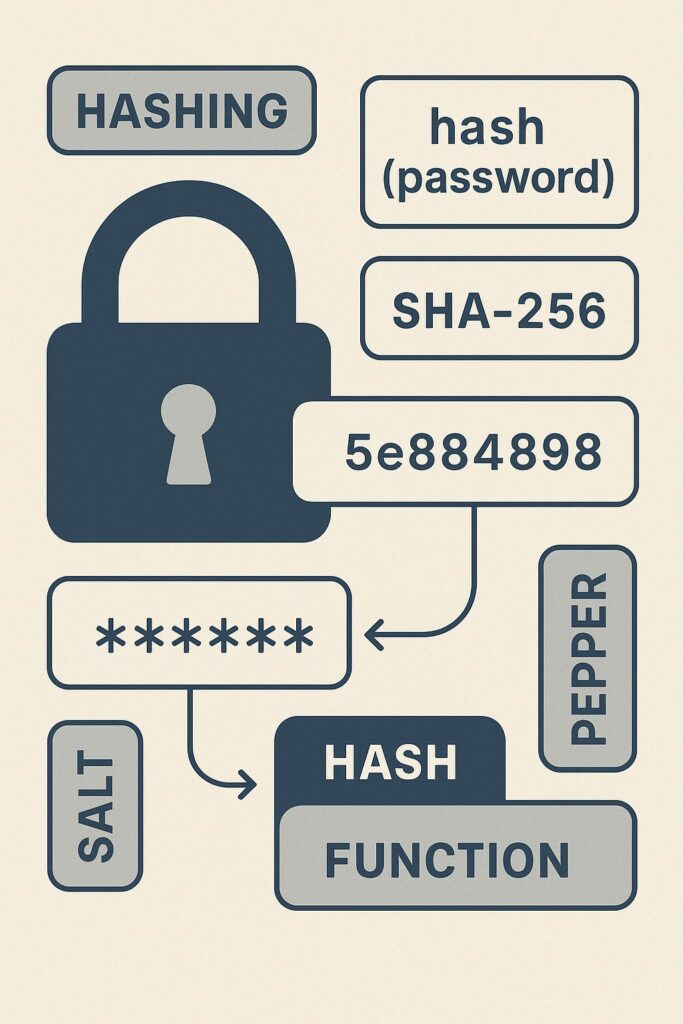
Explore the fundamentals of password cracking, beginner-friendly insights into how passwords are protected, attacked, and understood in cybersecurity.

So, you want to know how to make money cracking passwords? Well, then, let me point you in the right direction with a warning.

Learn how to quickly Download Private SoundCloud Audio Files by using SoundCloud’s API.

How to deploy Sysmon and keep it up to date at all time. Don’t waste your time managing Sysmon, just do this.

Do you want to deploy a script or software quickly via Group Policy? Learn the fastest software or script deployment method in Group Policy.

Are you planning on attending DEF CON 32? Check out my guide if this will be your first DEF CON. The helpful tips you need to maximize your DEF CON 32 experience.

A step-by-step guide to building a WinFE bootable live OS ISO file for Incident Response or troubleshooting.
