So, you want to know how to make money cracking passwords? Well, then, let me point you in the right direction with a warning.
Password hash cracking is incredibly fun and addictive—so much so that I find myself waking up in the middle of the night to check my phone for hash crack updates. I have Telegram set to get notifications of every cracked password, with a whip-cracking sound as the ringtone. Coming up with an attack on a keyspace, starting the attack, and then hearing that whip-crack fire off a dozen times is intoxicating.
However, password cracking may not be for everyone…
Prerequisite Warning
The following blog post will assume that you have an understanding of hash cracking and some of the more common hash cracking tools, such as Hashcat and Hashtopolis. This post is not meant to be an introduction to password cracking. It is for those who already have some experience cracking passwords.
Making Money Password Cracking – An Honest Accounting

Before we discuss how to crack passwords for money, we need to discuss the reality of password cracking and your motives. While password cracking is fun, it will likely not be profitable for you.
An honest accounting of the hardware and electricity required for password cracking will quickly dwarf the dollars earned.

Don’t get me wrong, there are some hashes with big bounties on them, but cracking them could take years, and that’s not guaranteed. So if your motivation is for a money-making side hustle, this ain’t it. If you are here because guessing people’s passwords sounds like a game to you, then you are in the right place.
How To Make Money Cracking Passwords
The short answer to making money cracking passwords is to use the website Hashes.com. Hashes.com acts as a third-party escrow service for hash cracking. The website itself does not do any hash-cracking; it is simply the middleman between hash Uploaders and hash Crackers.
Vocab Context
Uploaders == A user with a hash or list of hashes(hashlist) that needs to recover the original plain text password.
Crackers == Users who work to recover the plain-text passwords of hashes posted on the site.
Here’s how the process works.
The Uploader will upload their hash or hashlist to the website with a bounty of how much they’re willing to pay if someone is able to recover the plain-text password. The Hashes.com website will hold the uploaded hashes and bounty funds in escrow and post the uploaded hashes to the escrow section of the website.
When a Cracker recovers a password hash, they have to upload the original hash with the plain-text password recovered. Hashes.com will then verify the plain-text password does, in fact, equal the hash. If the verification process checks out, the bounty is released to the Cracker.

Payments are in cryptocurrency, either Bitcoin, Monro, or Litecoin. The Uploader chooses which type of cryptocurrency they pay with, and whatever the Uploader chooses is what the Cracker will get paid in. The cryptocurrency type and amount are clearly posted upfront on each hashlist.
As a password cracker, you compete with all other password crackers to submit found(cracked) hashes. The first user to find the plain-text password is rewarded with the bounty.
The Password Cracking Race
So, now that we know we are in a race to crack passwords faster than anyone else, we need to determine how to optimize the process best.
To start, we have to pick an attack method and then streamline and automate the cracking life cycle. We already have Hashtopolis to keep our attack commands, wordlists, and hashlists organized. Additionally, we can quickly and easily expand the total hashrate by adding more cracking agents to Hashtopolis.
What we need now is a way to take hashes from Hashes.com, get them into Hashtopolis, run an attack, and submit the recovered passwords back to Hashes.com.
Luckily, both Hashtopolis and Hashes.com have an API, so we just need a go-between to go between them.
This is the point where you will need some programming experience. You will need to put together a script that can perform some of the most common tasks between Hashtopolis and the Hashes.com website.
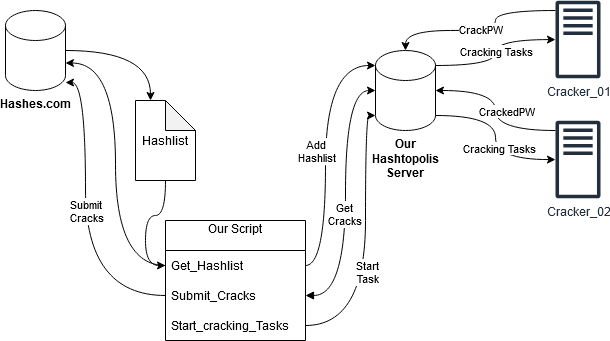
The most important function you should focus on first is automatic cracked hash submission. Getting your cracked hashes in quickly is key if you want to claim the bounty first. All other functions beyond that are just quality-of-life improvements.
Jump-Start Your Script
I have put together some of the Python scripts I use for my API calls to Hashes.com, Hashmob.net, and Hashtopolis. These are pretty quick and dirty, but they should at least help you jump-start your own script. The URL is below.
https://github.com/Brets0150/CG_PasswordCrackingAPIs
There is also the “hashes.com-cli” GitHub project, which can be used as a good reference for building your script.
Develop A Password Cracking Strategy
Having a password-cracking strategy is core to getting consistent returns. I have two main methods, and both have had good returns for me.
New Upload with Old Known Cracked Wordlists
This method goes after the low-hanging fruit. New hashes are uploaded every day. We want to grab those hashes and run them against the most common password pattern attacks. This method works best against a salted hash. Unsalted hashes are not unique and are likely to be cracked via the automatic lookup system. Since you want to grab new hashes daily, build an attack or set of attacks that will finish within 24 hours, so you can then pull in new hashes.
Old Uploads with New Keyspace Attacks
This method goes after older hashes, meaning posted for a long time without a crack, with an attack on a keyspace no one else has tried. I call this “finding the unmined vein,” and it can have very consistent returns. It can be difficult at first to find a keyspace that has not been thoroughly covered, but they do exist. These types of attacks typically require you to build your own wordlist and tailored rule sets. I found an unmined keyspace using a two-word combo recently and had over 30 days with dozens of cracks daily, some of which were worth .50 cents for one crack.
Password Cracking: Hold on, Is This Legal?
Is password cracking legal(in the US)? First off, I am no lawyer, just some guy on the Internet. So, do not consider this legal advice. However, this is my best understanding.
Similar to Penetration testing, authorization, and intent are crucial to determining legality. US Federal Law 18 United States Code(U.S.C.) section 1030, AKA: The Computer Fraud and Abuse Act (CFAA), is the main federal law used to prosecute computer crimes. The specific section related to passwords is 18 U.S.C. 1030(a)(6) and states the following.
(6) knowingly and with intent to defraud traffics (as defined in section 1029) in any password or similar information through which a computer may be accessed without authorization
If you read the law, you will see the words and phrases “knowingly,” “intentionally,” and “with intent to” frequently. So, if we, as password crackers, have knowledge that hashes are not obtained with authorization, or used for unauthorized uses, then we would be in violation of the law.
Password recovery-as-a-service (PRaaS) with authorization is legal. Many companies occasionally need PRaaS. I first got into password cracking because of one such need. In my case, A client’s network administrator unexpectedly died, and only that admin knew passwords to key systems. Some systems were reset, while others could not be reset without significant disruptions. So, I started with the hashes in the Cisco config backup files. After cracking that hash, we had a good idea of the network admin’s password pattern, making the recovery of other systems easy. My point here is that password cracking is not a shady, illegal business. It is a genuine service individuals and organizations occasionally find themself in need of.
TLDR: Password Cracking for Fun and Profit
Password cracking is very fun, and you can make some money performing Password recovery-as-a-service (PRaaS). However, don’t expect to make a ton of money, and be prepared to spend days researching, programming, and testing your password-cracking tools and strategies. Not a problem if you enjoy this sort of thing, but it’s not for everyone.
To be successful in password cracking and make some money, you have to do the following.
- Develop a cracking strategy.
- Build a script to automate and streamline the cracking process between multiple systems.
- Research, research, research.
- Build custom wordlists and rules.
As a final tip, if you want to be successful, you have to develop your own wordlists and rules. This means you need to analyze password patterns to find password keyspace others may have missed.
Now go forth and find every GPU and CPU you have and put them to work cracking hashes!
Happy Hunting!