
I have been working to upgrade my home networking infrastructure for some time to better monitor, secure, and manage vulnerabilities. The monitoring side is pretty easy, Nagios to monitor uptime, Rsyslog, and OSSec for OS security. However, I needed to centralize these tools and I wanted to have a TAP for all WAN traffic. There are a few ports NAT-ed I allow in from the WAN to a DMZ for remote access; OpenVPN Server, and a web control tool. So in addition to locking those points down, I wanted to be able to sniff and monitor the traffic ingressing and egressing my LAN network.
The first solution I tried was upgrading my router to one running OpenWRT because its OS supported the “TEE” iptables command. This did work but had two negative impacts.
- Messed up routes that came in over the VPN tunnel. Routing over the VPN would stop because the traffic would loop.
- Doubled the router’s workload, slowing down traffic internal and external. The CPU usage is pretty big, and the little ARM processor can only do some much.
After the shortcomings of the “Tee iptables” I bought a Cisco WS-C2960G-8TC-L for $60 off Ebay. The switch was put right in front of my main server and worked pretty well for a time, but also had some drawbacks.
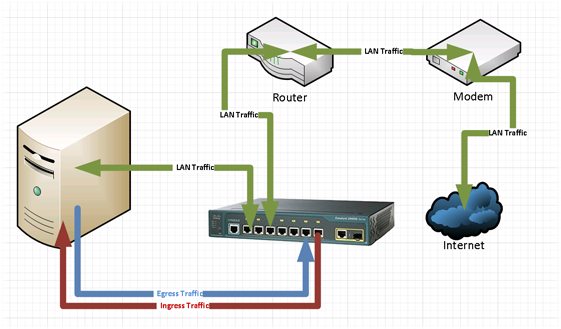
Switch SPAN Shortcomings
- To capture traffic for one port on the switch, you have to create two SPANs. One SPAN for incoming traffic on a port, and one for outgoing traffic on a port. This is a limitation of the switch itself, not the OS. So to capture all traffic on one port of the switch I needed two other ports on the switch and two on the server to dedicated to as TAP ports.
- This solution was limited to only capturing traffic that moved between the router and the switch; missing all the Wifi traffic. I could get around this by adding more hardware but that was just too much. Additional hardware adds unnecessary complexity and wastes more electricity to accomplish the same amount of work.
I finally gave in a bought a real hardware TAP. Network TAPs are kind of a niche item, so the available ones are expensive. The most reasonably priced one I found was the SharkTap Gigabit Network Sniffer made by midBit Technologies. The $180 price point is really good compared to the average $500 cost for Network TAPs.
The TAP sits between the cable modem and the core network router. So it can capture all traffic ingressing and egressing my network. The device is extremely simple to install, it is plug-and-play, no set up needed. There is a cheaper option that I tried first, and that was to get a 100Mbps version of the SharkTap. The 10/100Base-T ethernet version of the SharkTap is about $90 cheaper. This would have been fine since my ISP uplink is only 70Mbps down and 6Mbps up. However, I ran into an issue when I tried to deploy it. After a lot of troubleshooting in the OpenWRT OS, I found that the OpenWRT OS refused to set my WAN port to 100 Mbps port speed. This is when I just ordered the 1G version, and problem solved.
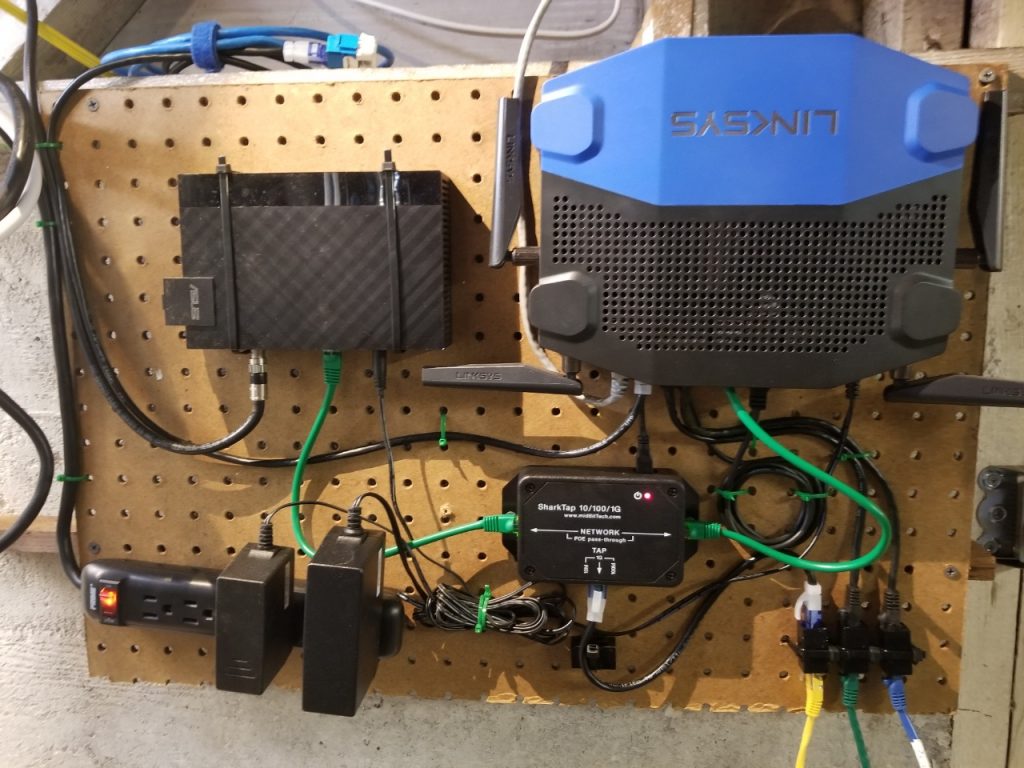
Now that the hardware is all in place, I built out a new logging server to capture, sniff, and log the data. I picked up a SuperMicro server from Ebay with an Intel E3-1240 CPU for about $220. The Intel E3 CPU is perfect for this job, it has low power consumption needs and has enough processing speed to handle sorting and sniffing 100Mbps of network traffic. Plus the Motherboard has two 1Gbps ports; one for network access and the other for TAP traffic capture.
The new server runs the latest version of SecurityOnion, a complete IDS/IPS operating system. SecurityOnion is quick to install and set up but has a steep learning curve on how to use the system.
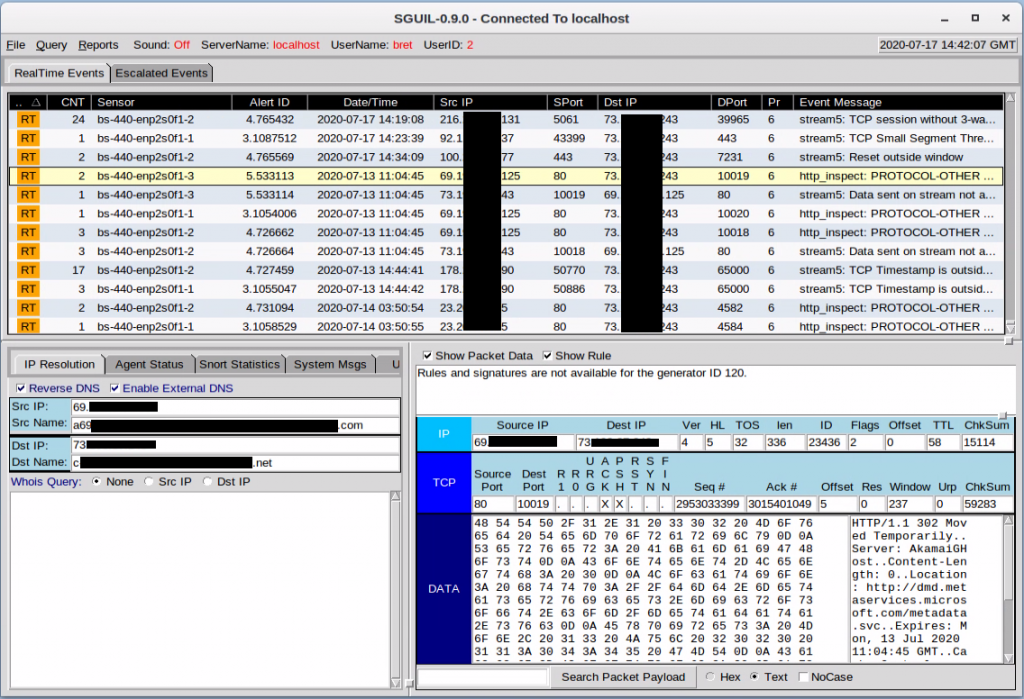
Within the first day, I found a serious issue with an IoT device on my network. SecurityOnion highlighted and alerted to some plain text outbound network traffic that held sensitive information. This led to an investigation into the IoT device and the discovery of some vulnerabilities in the firmware. I will disclose those discoveries at a later time once the vendor has a fix for them.
I started this project thinking that a TAP and traffic sniffer for a home network was overkill and that I would only catch a lot of external port scans. However, this was not the case at all and I am glad I invested in the hardware.














Leave a Reply