If you have ever thought about how you can help defend the Internet from online attackers, then I am here to show you how. The history of the Cyber Security community is filled with individuals who donate their time, skills, resources to making the Internet safer. Collectively these defense efforts have limited or even stopped many attacks.
The key to defending such a large Internet ecosystem is to gather a massive amount of telemetry data about attacks. To collect the amount of data needed requires tens of thousands of endpoints submitting their logs to one place. This is where the Internet Storm Center steps in, and you can help by running your own honeypot server!
Short on time? TLDR

SANS Internet Storm Center
The Internet Storm Center(ISC) is a project sponsored by the SANS Institute but is driven and built by a volunteer Cyber Security Community. ISC’s goal is to detect, analyze, and warn the Security Community of emerging threats.
The ISC relies on an all-volunteer effort to detect problems, analyze the threat, and disseminate both technical as well as procedural information to the general public. Thousands of sensors that work with most firewalls, intrusion detection systems, home broadband devices, and nearly all operating systems are constantly collecting information about unwanted traffic arriving from the Internet. These devices feed the DShield database where human volunteers as well as machines pour through the data looking for abnormal trends and behavior. The resulting analysis is posted to the ISC’s main web page where it can be automatically retrieved by simple scripts or can be viewed in near real time by any Internet user.
https://www.dshield.org/about.html
Contribute To The ISC
There are a few ways you can contribute to the ISC project. The primary method is by providing data to ISC through DShield Sensors. DShield is how volunteer contributors submit log data to ISC for analysis. Submitting data to DShield is done through client-side log collection tools. Most major operating systems(OS) and firewall OSs have a client module you can install to send data to DShield. See this link for a complete list of supported DShield Sensor clients. However, if you really want to contribute, set up a DShield Honeypot.
Running a Honeypot
One of the most valuable ways to contribute to the ISC and cyber security community is to set up a simple honeypot. The DShield Honeypot is a set of scripts and tools that make building a low interaction honeypot quick and easy. Once set up, DShield begins to gather data from the IPs it sees conducting malicious scanning and attacks.
The DShield Honeypot gathers the following data points.
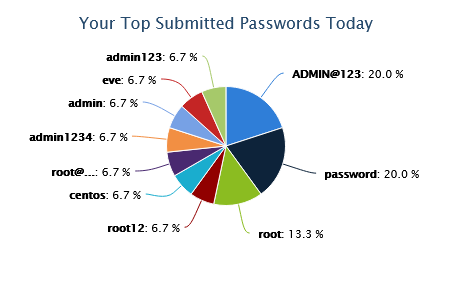
- SSH and Telnet usernames and passwords.
- Full HTTP requests.
- Firewall logs for traffic on all ports.
DShield Registration
Registering with the ISC is encouraged but is not required. I recommend you register since it gives you access to a bunch of features and data you will find helpful. Plus, you can sign up for the ‘Fightback’ program. ISC will analyze submitted log reports and pick strong cases to forward to the ISP from which the attack originated.
Register here!
Once registered you can log in and obtain an API key from your account. Use this API key to register your DShield Honeypots.
Installing DShield Honeypot
DShield Honeypot has two main recommended build-out options; on a Raspberry Pi or a Ubuntu 20.04 VM. If you want to run this honeypot out of your home, the Raspberry Pi is the best option. There is an excellent and in-depth video that covers the Raspberry Pi build-out. The Ubuntu 20.04 VM is a better option if you have private or public cloud infrastructure, a WAN IP, and a small number of system resources to spare. Either option you choose, you need to understand that this R-Pi or VM has to be dedicated solely to DShield only.
DShield Honeypot on Ubuntu 20.04 VM
I have access to several Cloud Hosting solutions, so I prefer the Ubuntu 20.04 VM. So let’s run through the build-out and installation of the DShield Honeypot.
DShield Honeypot VM Requirement
The system requirement for a DShield Honeypot is minimal. I built my Ubuntu VM with 1x CPU, 1GB RAM, and 20GB disk space and had no issues. You should also use one dedicated WAN IP address for the VM.
Cloud VM Firewalls
Most Cloud platforms have a built-in firewall separate from the VMs firewall. You should configure the Cloud firewall to pass all ports from the WAN IP directly to the VM. We need to forward all the ports to the VM so that DShield can see all incoming traffic. DShield will configure the VMs firewall, so don’t stress over forwarding all ports from the Cloud firewall to the VM.
Install DShield
Install, IP, and set up a strong user password on the Ubuntu VM. Then start the DShield install.
# Update the core OS and packages.
apt update && apt -y dist-upgrade && apt autoremove
# Install the basic required packages.
apt install -y git openssh-server
# Reboot to allow any kernel update to be applied.
reboot
# Clone the DShield repository.
git clone https://github.com/DShield-ISC/dshield.git
# Run the DShield installer.
# During the install you will be asked for your email and API Key.
./dshield/bin/install.sh
# Reboot to apply the changes
rebootAfter rebooting, the SSH port will change to port 12222. SSH into the VM and confirm that the DShield VM is operating as expected.
# Confirm DShield is running correctly.
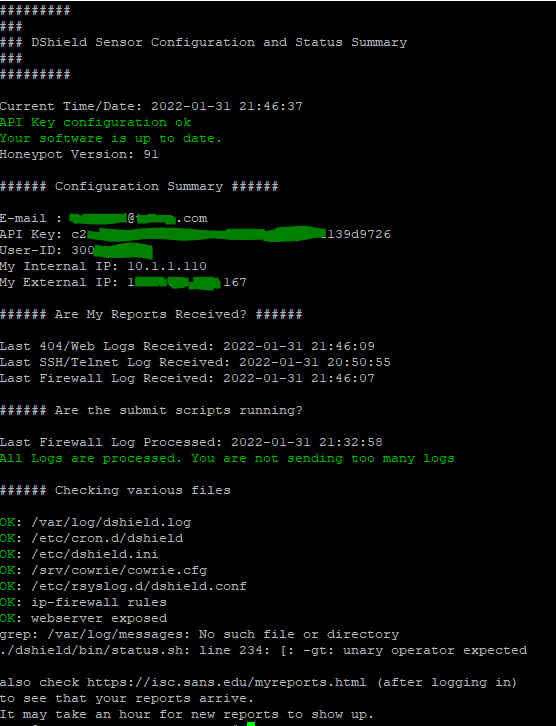
./dshield/bin/status.sh
# Add the following line to cronjobs to ensure DShield stays up to date.
# Check for updates weekly at 5 AM and reboot.
0 5 * * 1 /root/dshield/bin/update.sh && rebootYour status should look like the below image.
If everything is green then you are all good and the installation is complete!
The Data
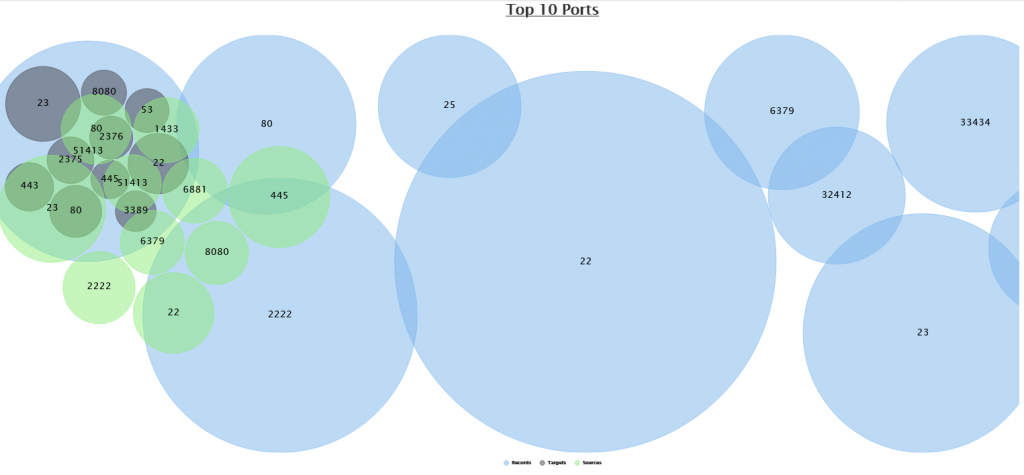
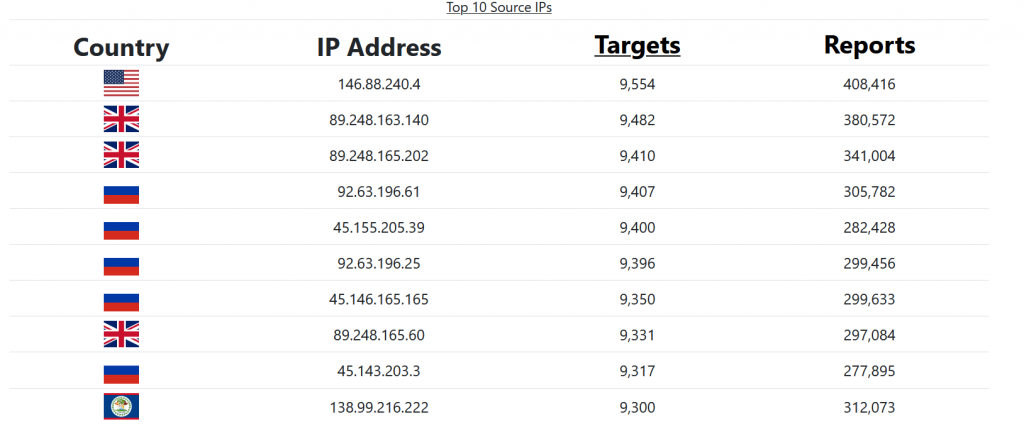
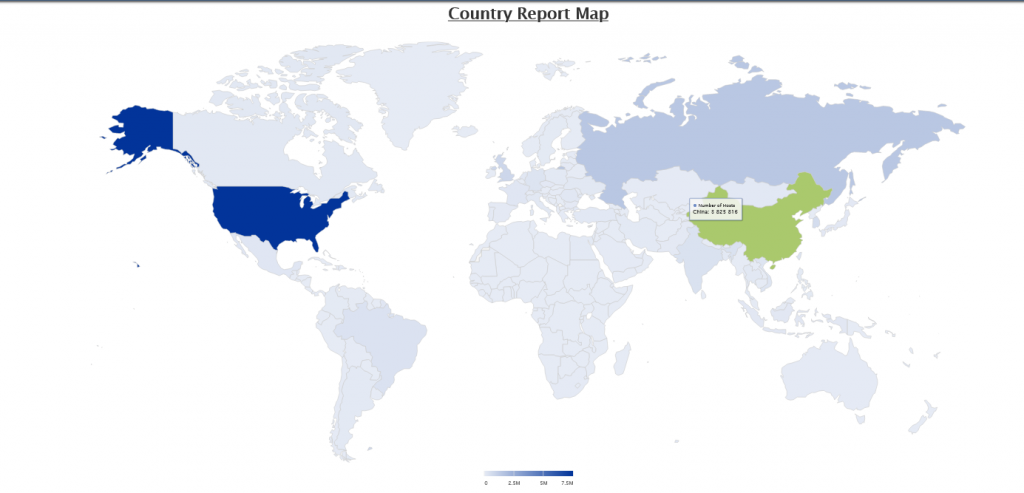
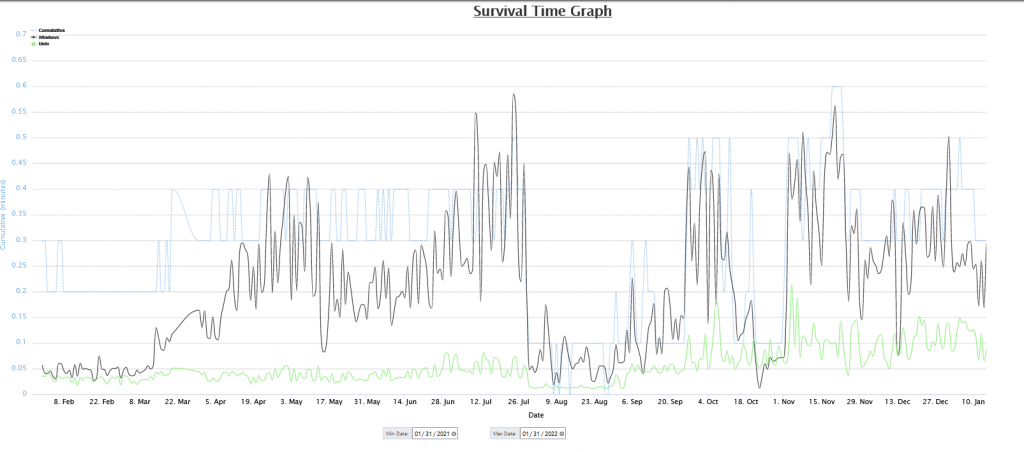
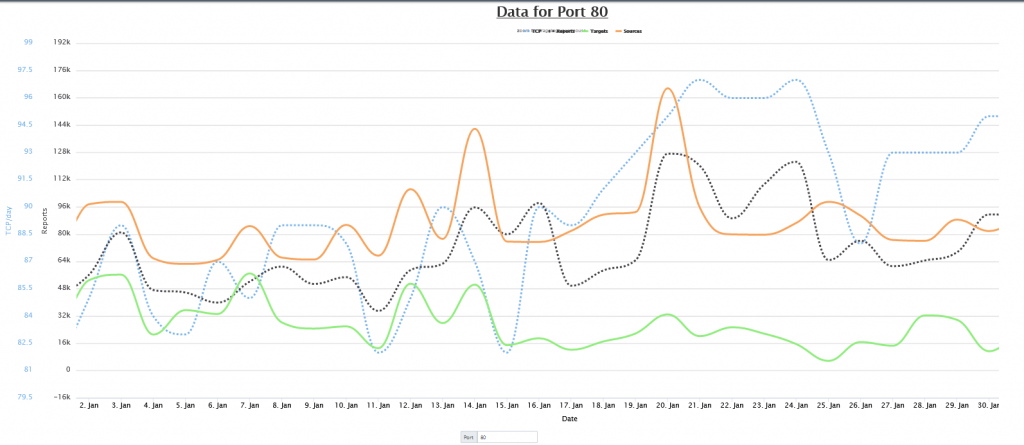
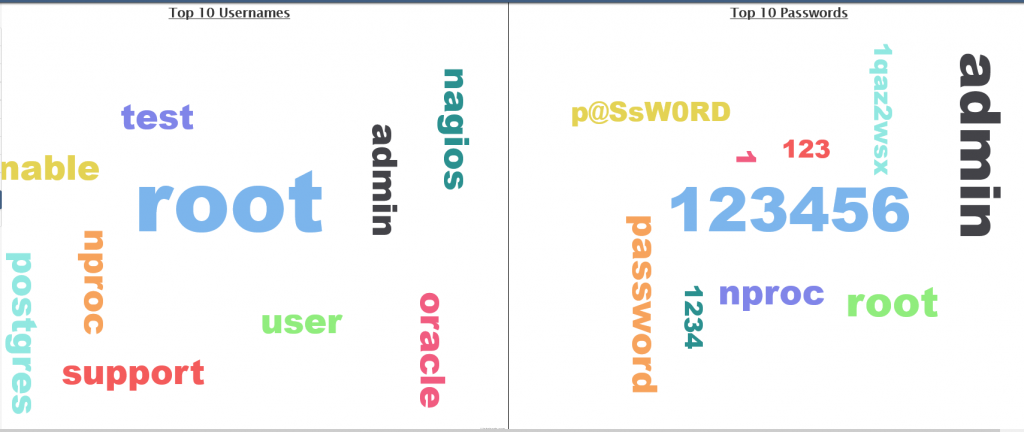
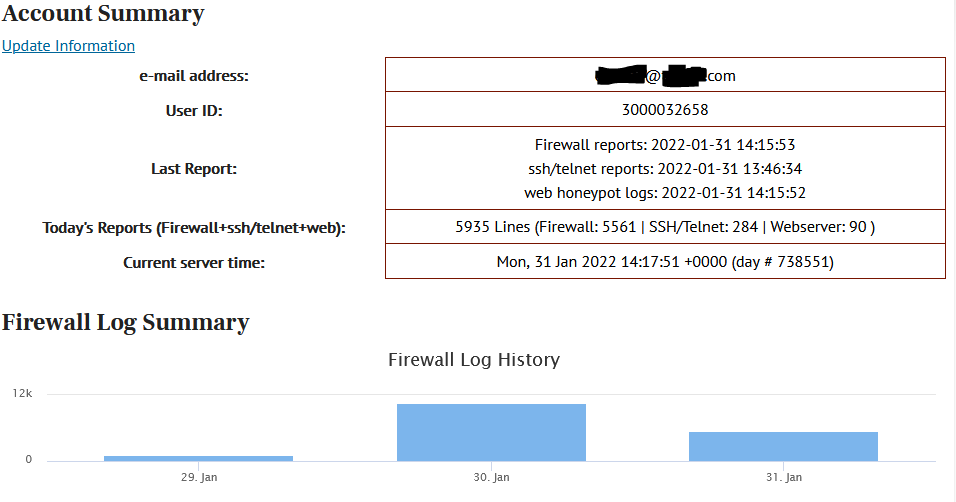
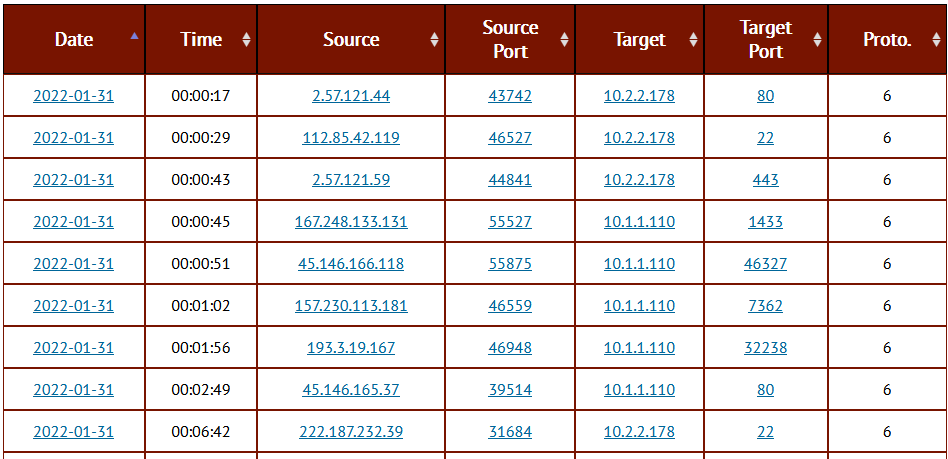
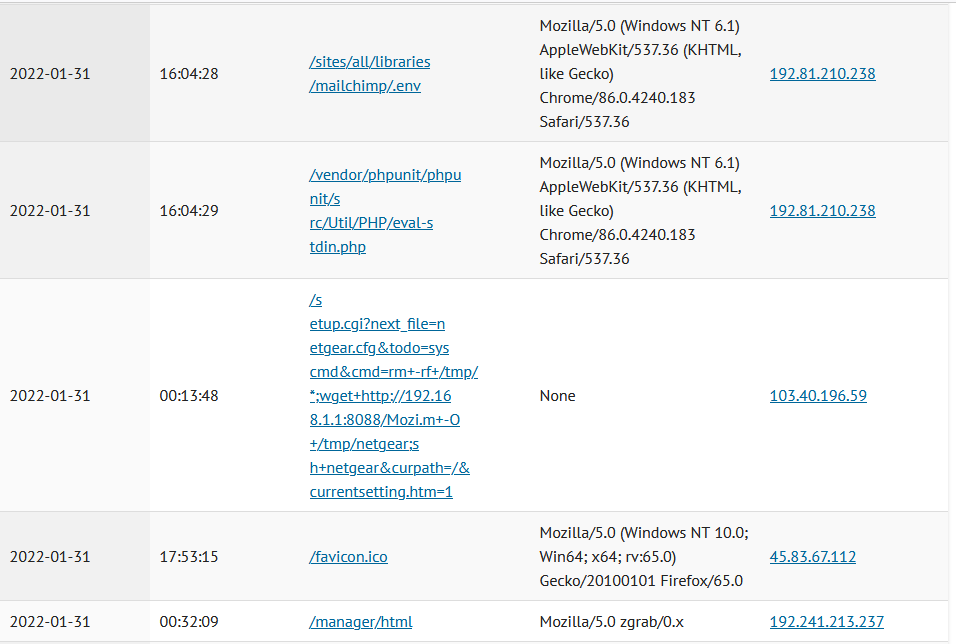
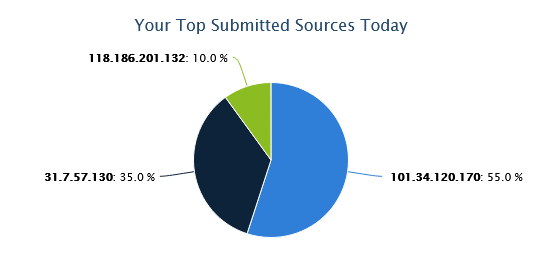
After a few hours, your ISC portal will begin to fill with data of the traffic targeting your honeypot. You can view this data on the “MyReports” page. There are three different reports pages for Firewall logs, HTTP requests, and SSH/Telnet requests. Each report has great data about the attack targeting us daily.
Firewall Data
HTTP Request Data
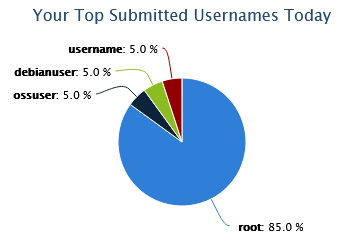
SSH/Telnet Data
TLDR: Too Long Didn’t Read
- The Internet Storm Center is a volunteer community collecting data about online attacks. This data informs the community how to defend against attacks.
- You can help by submitting logs or running a DShield Honeypot.
- Installing DShield Honeypot on Ubuntu 20.04 VM is quick and straightforward.
- If you register, you will gain access to the data you gather, which can help you form a better defense of your networks.
Running a SOC/NOC?
Check out the ISC data dashboard! It is great eye candy for any SOC or NOC.