In this article, we are reviewing Apache’s default settings. Apache out-of-the-box will display internal IP addresses, OS version, Apache’s version, Apache modules, and more. On its own, leaking this data is not a big deal, but in combination with other information, it may enable an Attacker. Regardless, we should always try to minimize the data we are giving out about our systems.
This article is the second in the Diamond Hard LAMP series.
Default Site Index & Error Pages
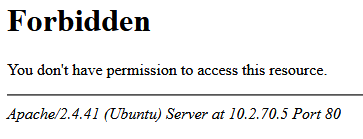
What’s the first thing an Attacker will do after port scanning an IP and discovering port 80 or 443 open? Easy, the Attacker will open the server IP in a web browser. Here the Attacker will find the details about the server software versions, and this is the first step in exploiting the system. With the version numbers, an Attacker can search for known vulnerabilities in Apache, our OS, and modules. To prevent this we will add new default site error files that will replace the standard error messages. The new error pages will give away no details about the system. Run the below commands to produce the new simple error pages.
echo "<h1 style='color:red'>Error 404: Not found :-(</h1>" > /var/www/html/custom_404.html
echo "<p>Sorry, but I cannot find that file.. Are you sure you typed in the correct URL?</p>" > /var/www/html/custom_404.html
echo "<h1 style='color:red'>Error 404: Not found :-(</h1>" > /var/www/html/index.html
echo "<p>Sorry, but I cannot find that file... Are you sure you typed in the correct URL?</p>" > /var/www/html/index.html
echo "<h1>Bonk! Something went wrong...</h1>" > /var/www/html/custom_50x.html
echo "<p>Hmm.. We seem to be having some technical difficulties. Hang tight.</p>" > /var/www/html/custom_50x.htmlNow we need to edit the “/etc/apache2/sites-available/000-default.conf” file to use the new error pages we added. Edit the “000-default.conf” file to match the below text.
<VirtualHost *:80>
ServerAdmin webmaster@localhost
DocumentRoot /var/www/html
ErrorLog \${APACHE_LOG_DIR}/error.log
CustomLog \${APACHE_LOG_DIR}/access.log combined
ErrorDocument 401 /custom_404.html
ErrorDocument 403 /custom_404.html
ErrorDocument 404 /custom_404.html
ErrorDocument 405 /custom_404.html
ErrorDocument 410 /custom_404.html
ErrorDocument 411 /custom_404.html
ErrorDocument 412 /custom_404.html
ErrorDocument 413 /custom_404.html
ErrorDocument 414 /custom_404.html
ErrorDocument 415 /custom_404.html
ErrorDocument 500 /custom_50x.html
ErrorDocument 502 /custom_50x.html
ErrorDocument 503 /custom_50x.html
ErrorDocument 504 /custom_50x.html
</VirtualHost>Lets take a look at the differences the changes made.
Before
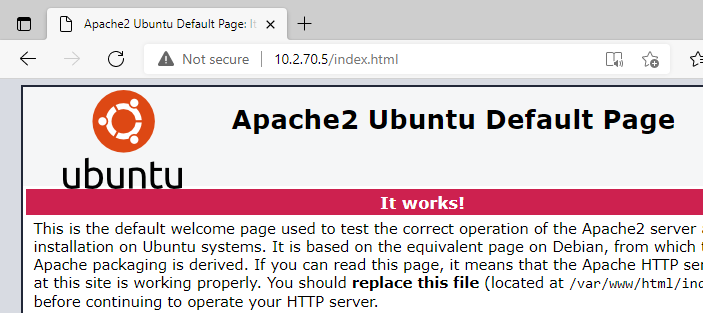
index.html 
404 Error
After
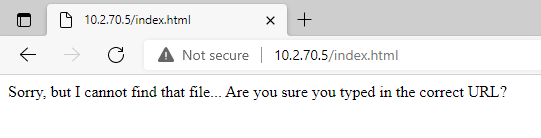
Index.html 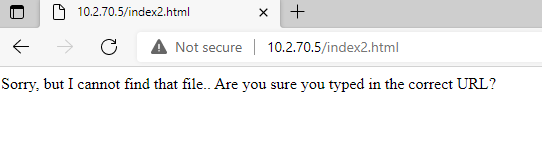
404 Error
Prevent Apache Header and Footer Data Leaks
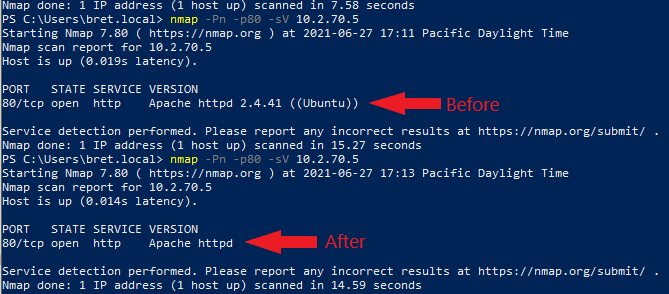
Apache by default leaks the server’s OS-type and enabled Apache modules data in the way it responds to HTTP requests. This allows port scanners like Nmap to quickly determine the OS and Apache version. So when a vulnerability is discovered in Apache, the vulnerable system can be quickly found and exploited by malicious bots online. To prevent this we just need to modify two simple configuration settings.
ServerSignature Directive
The
https://httpd.apache.org/docs/2.4/mod/core.htmlServerSignaturedirective allows the configuration of a trailing footer line under server-generated documents (error messages,mod_proxyftp directory listings,mod_infooutput, …). The reason why you would want to enable such a footer line is that in a chain of proxies, the user often has no possibility to tell which of the chained servers actually produced a returned error message.
ServerTokens Directive
This (ServerTokens) directive controls whether
https://httpd.apache.org/docs/2.4/mod/core.htmlServerresponse header field which is sent back to clients includes a description of the generic OS-type of the server as well as information about compiled-in modules.
ServerTokens & ServerTokens Config Fixes
Just add the two below lines to the bottom “/etc/apache2/apache2.conf” file. After the changes restart Apache.
ServerTokens Prod
ServerSignature Off Now that we have made our changes to ServerTokens & ServerTokens, let’s test with Nmap to see the difference.
Final Notes
This hardening method is not a surefire way of preventing a server’s Apache version, module versions, or internal IP from leaking. We are just making that data harder to find, and harder for automated attacks against us.











1 Pingback