
There is active threat intelligence in your email inbox. Spam email campaigns are not just an annoyance, they are a leading method of data breaches. The intelligence we gain from analyzing these threats will show how we can build better defenses.
Over the last year, the strategies of ransomware attackers to gain access shifted. As organizations put resources into protecting internet-facing systems, an old tactic returned. Attackers refocused to users with a new level of sophisticated spam email campaigns. Spam messages are indistinguishable from the emails you would get from a coworker, boss, or an outside vendor. Gone are the days of the Nigerian Prince scams. Analyzing targeted spam will tell us more about our enemy and what they know about us.
Short on time? TLDR
Starting in late 2020 our company was inundated with highly targeted spam emails with malicious attachments. I work for a Managed Services Provider, and our team is almost entirely IT Professionals who know the indications of spam. However, the rise in spam messages was still concerning. I wanted to eliminate these messages from even making it into anyone’s inbox.
Below is one of the example spam messages. I should note that we have an Indonesian Team we work with, and the email is in their native language.
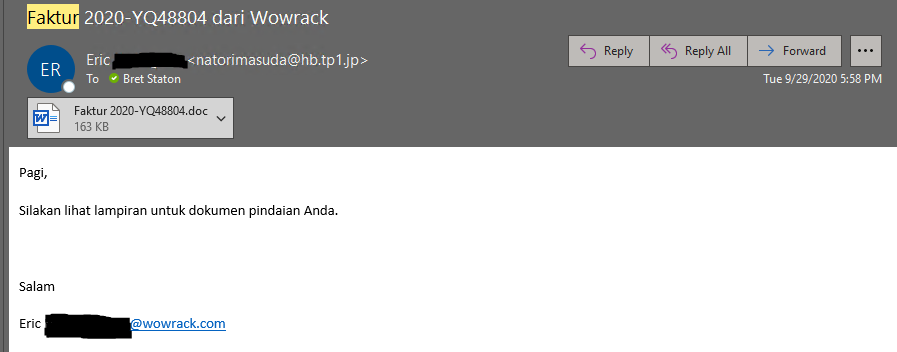
The message reads, “Good morning, Let me know if you have any questions. thanks. Best regards”. This message was sent to many members of our team. To someone in billing, for example, this email may have looked ok to open.
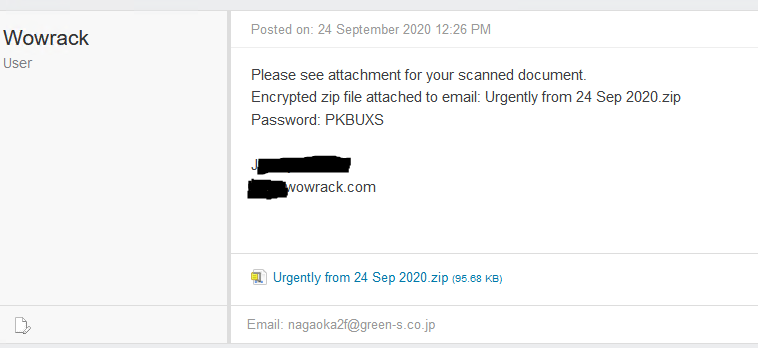
Below we have another example spam message. This one is better than the first and might suggest the attacker spent a little more time considering his attack. This message was sent into the ticking system where many more users would see it. The malicious file was encrypted so it could by-pass the spam and anti-virus filters. They also got the language correct this time.
Threat Analysis
What can we learn about the enemy’s intel from this spam message? Well, quite a lot. First, they know we have an Indonesian Team, which is no secret. They know some of our email addresses, but which ones? Putting together a list of email addresses receiving that message reveals only publically known emails were attacked. It is also clear the enemy does not know who has what job role in the company. Sending an invoice(Faktur means invoice) to the security guy does not make a lot of sense. This attacker seems to possess only publicly available information. That is not to concerning at this point. It also appears they have not spent a lot of time on reconnaissance, merely email address collection. We are likely one of many companies targeted by an automated reconnaissance tool that gathers details to craft customized spam emails. Nothing too fancy.
Malicious Macro File
Let’s analyze the attachment to see what the goals of the attacker are. There are many ways to dissect a malicious macro file. However, it takes an understanding of multiple disciplines like VB Programming, Powershell, deobfuscation methodologies, and Windows Management Instrumentation. I highly recommend learning these topics. I will list some resources and tools at the end to get you started.
For the sake of time, there is an easier way.
There is an excellent free online forensic resource I have been using to run analysis on malware. Any.Run is an online sandbox designed to have malware run within it and generate reports. You can run and watch the malware in real-time with full logging details of what the malware is doing. The malware will be used to create indications of compromise(IOC) lists. With the IOC list, we can monitor and defend against similar attacks.
Let’s upload the malicious word file to Any.Run and see what it finds.
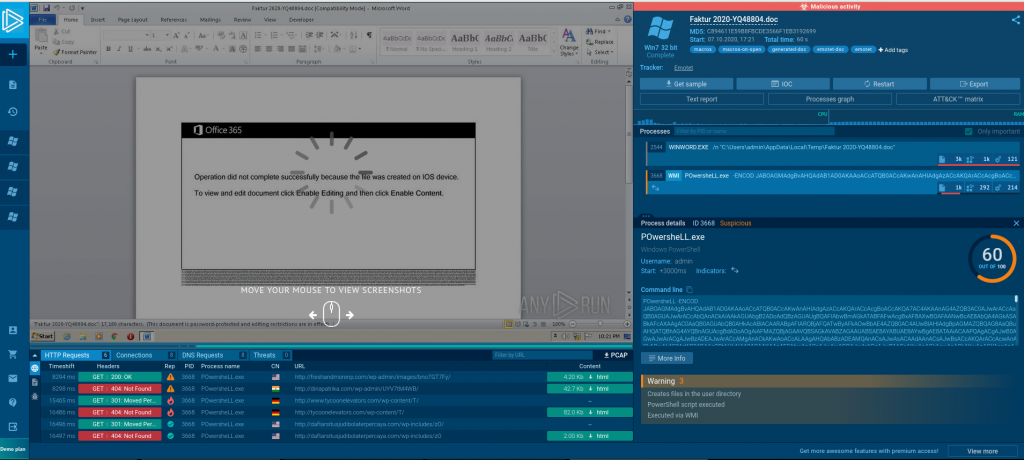
HTTP Request Made
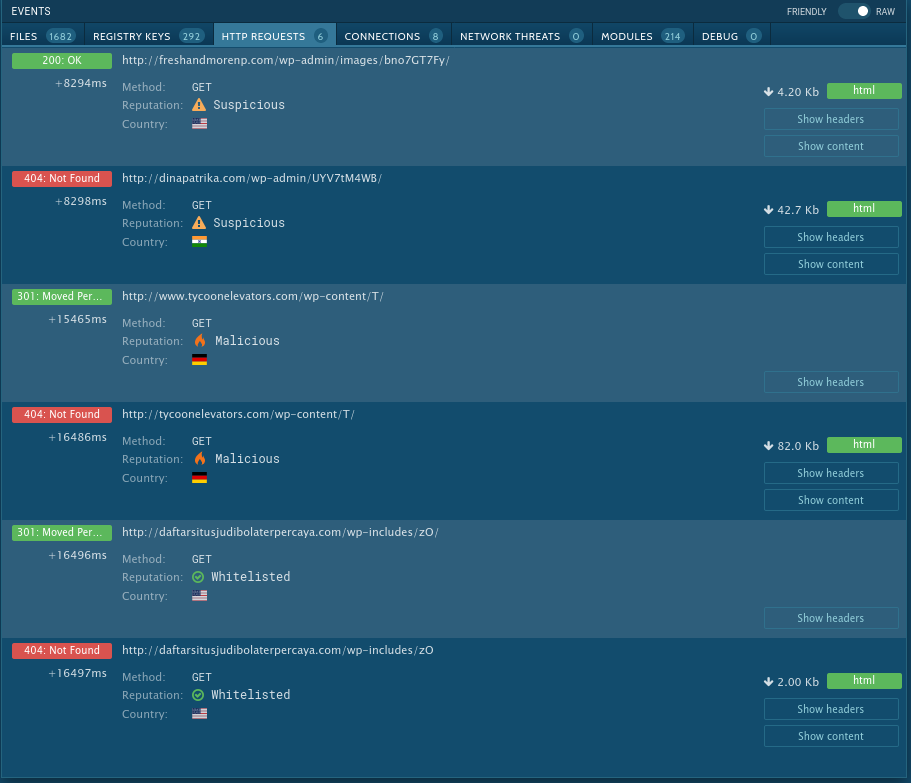
The Any.Run sandbox confirmed the obvious; this is a malicious macro word file. The VBA macro executes when the document opens automatically. Using the WMI the VBA macro executes an obfuscated Powershell script that is a Dropper Trojan. The Dropper Trojan calls out to a list of compromised websites that are running WordPress. The compromised WordPress sites are hosting a copy of the Backdoor Trojan. The Backdoor Trojan once downloaded and installed will call home to the Attacker’s Command and Control(C2) servers, establishing a persistent backdoor. The Backdoor Trojan used is identified as the Emotet Trojan.
What we know about Emotet
- One of the most dangerous trojans in use today.
- Targets corporate victims, not private users.
- It is well maintained and updated.
- Module payload design, for multi-purpose attacks.
- Used to download additional trojans.
- Has a worm component to spread infection through the internal network. SMB is commonly exploited for lateral movement.
- Indicators suggest Russian in origin.
Developing a Defensive Strategy
What can we learn about the Attackers from the malware sample we collected? The Emotet Malware is a widespread attack focusing on corporations. The attackers have built out malware distribution points all over the internet by exploiting WordPress vulnerabilities. My organization is not the main target, just one of many targets. The key in the infection chain is getting a user to open a spam email.
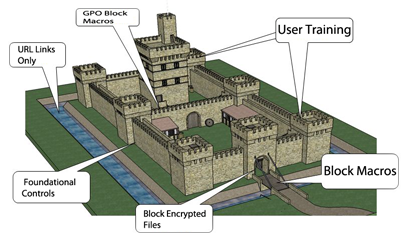
Now that we have a better understanding of what we need to defend against we can build procedural and technical controls to improve security.
Procedural Controls
- All employees will no longer email documents to each other. Instead, to pass files only link sharing is allowed. For example, a link to a Google Doc, Office 365, or internal SMB file share. The use of Google Docs and Office 365 has the added benefit of being scanned for malware when uploaded to their servers.
- Quarterly email security training for all employees. Ensure all users are regularly trained on how to spot spam emails.
Technical Controls
- Change the spam filter setting to block all emails that carry attachments with embedded macros.
- Change the spam filter setting to block all emails that carry attachments with encrypted archives.
- Block all macros in Office Suites via a GPO policy.
These controls will directly impact the risk of the malicious email campaign. I should note that I did not list other controls like ensuring Windows updates, Firewalls enabled, and strong Anti-Virus, since all these should already be basic foundational controls in place. Of all the controls listed above, User training cannot be stressed enough. The End Users are your weakest point and the last line of defense.
TLDR: Too Long Didn’t Read
Know Your Eneny
- Analyze attacks against your organization.
- Try to understand what your enemy knows about your organization.
- Understand the goal of your attacker and the tools being used against you.
- Analysis of malware can help you form a defensive strategy.
Tools for Malware Analysis
Short on Time?
- Any.Run Online Sandbox
Wanna be a Pro?
- Learn to use REMnux OS
- Olevba3 is a tool for Office Docs analysis
- Learn to use Ghidra
Developing a Defensive Strategy
Procedural Controls
- All employees will no longer email documents to each other. Instead, to pass files only link sharing is allowed. For example, a link to a Google Doc, Office 365, or internal SMB file share. The use of Google Docs and Office 365 has the added benefit of being scanned for malware when uploaded to their servers.
- Quarterly email security training for all employees. Ensure all users are regularly trained on how to spot spam emails.
Technical Controls
- Change the spam filter setting to block all emails that carry attachments with embedded macros.
- Change the spam filter setting to block all emails that carry attachments with encrypted archives.
- Block all macros in Office Suites via a GPO policy.











Leave a Reply