
Web servers are on the front lines of cyber warfare. Their publicly accessible nature makes them prime targets for exploits and attackers. Luckily there are many tools and methods to secure Linux web servers. Let’s review our Linux Web Server Security Hardening Checklist.
Building a secure Linux web server running Apache MySQL and PHP(LAMP) is not quick. There is no “button” to push to add security. It takes a concert of software working together to lock down and harden the web hosting services.
Here are the tools and techniques you need to know to build a Diamond Hard LAMP server.
Building the Foundation of a Secure Linux Server
Start with the basics!
Keeping a system secure starts by ensuring the OS and its packages are always running the latest version. Automate the update process to keep your system on top of its security updates. Don’t rely on System Admins to do updates manually! When choosing an OS pick one with Long Term Support(LTS). LTS OSs ensure patches and fixes will be available well into the future.
- Use only the newest versions of an OS.
- Use an OS with Long Term Support.
- Enforce a strong password policy.
- Don’t use the root user account; use Sudo.
- Turn on and configure the Firewall.
- Store passwords in slow BCrypt hashing algorithm.
- Keep the system up-to-date with automatic updates.
- Limit allowed IPs to management ports like SSH.
Click here to review the Linux Web Server Hardening: The Basics
Also, see Linux Server Hardening: Enforce Strong Passwords
Prevent Apache from leaking Server Details
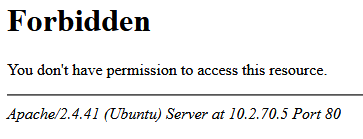
Apache out of the box will display internal IP addresses, OS version, Apache’s version, Apache modules, and more. Leaking this data on its own is not a big deal, but in combination with other information may give an Attacker just what they need.
Apache Hardening Checklist
- Replace default site page.
- Route IP based virtual hosts elsewhere.
- Prevent Apache Header and Footer Data Leaks
- Add default erorr pages
Click here to learn how to prevent Apache Information Disclosure
Hardening with Web Application Firewall
Add a Web Application Firewall(WAF) to filter malicious traffic from our servers. ModSecurity is able to monitor and alert on malicious web traffic in real-time. With this, we can better defend against attacks like SQL injection, XSS, Trojans, bots, session capture/hijacking, and many others. We are even able to write custom rules for any new type of attack we discover.
ModSecurity Hardening Checklist
- Install ModSecurity
- Apply latest ModSecurity rules
Click here to learn how to install and configure ModSecurity
Blocking Malicious Traffic with Fail2ban

Everything we need to block webserver attacks is right in our server logs.
Failed SSH login attempts, bots, and automated tools triggering thousands of errors, all of which will show up in our log files. So it’s crazy not to scan those logs for the IP addresses that are causing trouble and block them. There is no reason for an IP to fail an SSH login 100 times when doing something not malicious.
Fail2Ban Hardening Checklist
- Install Fail2Ban
- Configure Fail2Ban to block bad actors
- Have Fail2Ban work in concert with ModSecurity to block Layer 7 attackes.
Click here to learn how to install and configure Fail2Ban to block malicious traffic!
Sandboxing Web Applications

Web applications will have flaws, and those flaws will lead to unauthorized access. We can mitigate the risks of a vulnerable website by restricting the website’s access rights on the server. So in the event of a compromise, we will confine the damage to one website and not the whole server.
AppArmor Hardening Checklist
- Install AppArmor
- Build a AppArmor profile for each website.
Click here to learn how to install and configure AppArmor!
Security and System HIDS Monitoring

A Host-based Intrusion Detection System(HIDS) is a powerful and necessary tool to combat threats to our servers. We need our servers to tell us when there is an issue, and not rely on someone logging in to discover problems. A HIDS job is to monitor, analyze, and if needed alert us about its internal integrity.
There are a ton of great HIDS tools out there; paid and free. For those of us who have simple needs and cannot justify building a full Server & Host IDS, we can use a standalone install of OSSEC.
OSSEC Hardening Checklist
- Install OSSEC
- Configure alerting and filter false positives
Click here to learn how to install and configure OSSEC!
Strong SSL/TLS Settings

Configuring SSL/TLS settings in a Linux web server can be tricky. There are many details to get right. To make sure our SSL/TLS security is top-notch, we can use Qualys’s SSLLabs online tool. Let’s review how to get a 100% SSL/TLS Score on SSLLabs online testing tool.
SSL/TLS Hardening Checklist
- Generate a strong Let’s Encrypt Certificate
- Generate a unique Diffie-Hellman Key
- Enforce strong SSL/TLS settings.
- Configure CCA DNS records for a domain name.
Click here to learn how to configure and test strong SSL/TLS settings!

Diamond Hard LAMP
Why spend all this time building and configuring services when you can just use the Diamond Hard LAMP tool I created! All the above security hardening tools and techniques are incorporated into Diamond Hard LAMP. This makes deploying and managing a secure web hosting server simple and fast.
Click here to get started with Diamond Hard LAMP










