
Hardening Windows operating systems is complicated, and knowing when you have enough security can be challenging. There are many different components and security vs. convenience trade-offs to consider. Compounding the problem are the many OS host hardening standards and hardening best practices to choose from.
So in this blog post, I will discuss client OS hardening standards for Windows 10 & 11 clients and how you can test your system for weaknesses. By the end of this guide, you will have a system hardening checklist to start improving your environment.

Basic Client Hardening
Before adding more advanced system hardening recommendations, we need to ensure we have covered the basics. The basics OS hardening are things like…
- Using a fully patched and upgraded OS with long-term support.
- Remove unnecessary services, applications, and network protocols.
- Configure OS user authentication and remove default accounts.
- Anti-malware software, Host-based firewalls
- and more…
For a complete list of basic and generic OS hardening, I recommend reading the NIST’s Guide to General Server Security Publication 800-123.
How to Test Your Client OS Security
OK, let’s cut to the chase. You are here to learn how to test your client hardening and security to make improvements. I have found that organizations just starting the security improvement journey should start with the Center for Internet Security(CIS) Benchmarks. CIS has detailed, in-depth, thousand-page PDF documents on OS security hardening for nearly all OSs. Don’t be put off by the thousand-page document; there is also a tool for testing.

CIS Benchmarks are guidelines for securing technology against cyber attacks. They cover a range of technology types, including cloud platforms, containers, databases, and mobile devices. CIS Benchmarks map directly to CIS Controls to help organizations comply with industry regulations and frameworks while increasing security defenses.
Relax; There is a Tool to Help

We will use the CIS Controls Self-Assessment Tool(CIS-CAT) to evaluate how hardened our client systems are. The CIS-CAT is a tool provided by CIS with a free(Lite) and paid-for(Pro) version. We will be using the free version to run a CIS Controls Self-Assessment and produce a report of security weaknesses. You can use the CIS-CAT report as a baseline to start improving upon.
The CIS-CAT Lite version can only be run on one system manually. However, if you use Group Policies within Active Directory to fix the weaknesses discovered in the CIS-CAT report, you can improve security across the whole domain. In the future, once you have shown the value of the CIS-CAT tool you could petition your C-Levels for a budget to buy the CIS-CAT Pro. CIS-CAT Pro has many more features and improvements to manage security configuration compliance at scale.
Downloading CIS Controls Self-Assessment Tool(CIS-CAT)
Download a copy of the CIS-CAT Lite tool to one of your domain-joined Windows clients. You will need to complete a simple CIS request form(on the right-hand side of the website), after which you will be emailed a link to download the tool.
URL: https://learn.cisecurity.org/cis-cat-liteOnce you have the CIS-CAT portable program zip file, unpack the zip file and open the newly unpacked folder. Locate, right-click, and run the “Assessor-GUI.exe” executable file as Administrator within the folder.
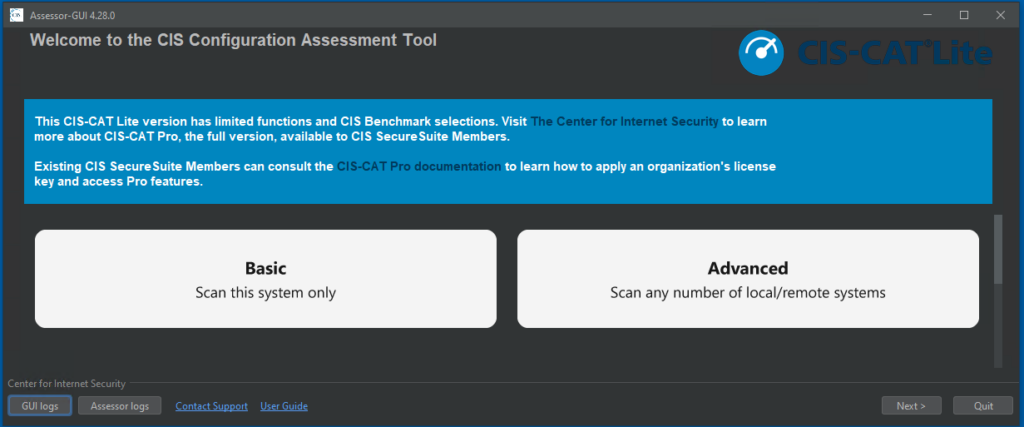
The CIS-CAT program does not need to be installed; it can run in portable mode. After starting CIS-CAT, start a new system test by clicking “Basic Scan this system only“.
Select the benchmark assessment you wish to run. The CIS-CAT application may automatically select and add the “Microsoft Windows 10 Enterprise Benchmarks – Level 1“. If you are running Windows 11, you will still use the Windows 10 Benchmarks; they are basically the same OS. Once you have the benchmark test added, click next to continue.
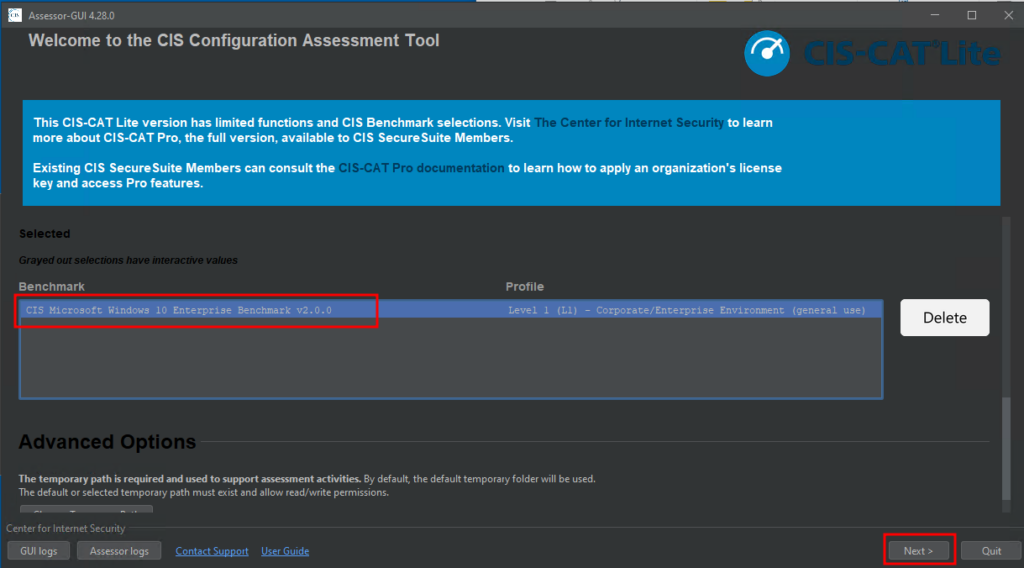
The next screen will have “Assessment Options.” You can ignore these and click “Next.” You will then be asked if you want to start the testing; click “Start Assessment” to begin.
The test will kick off and take a few minutes to run.
Go get a cup of coffee; this step is not optional!
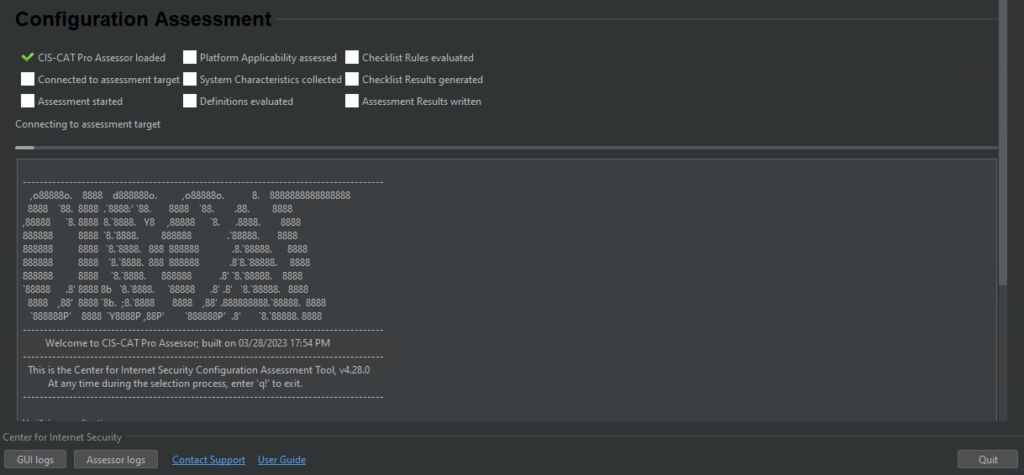
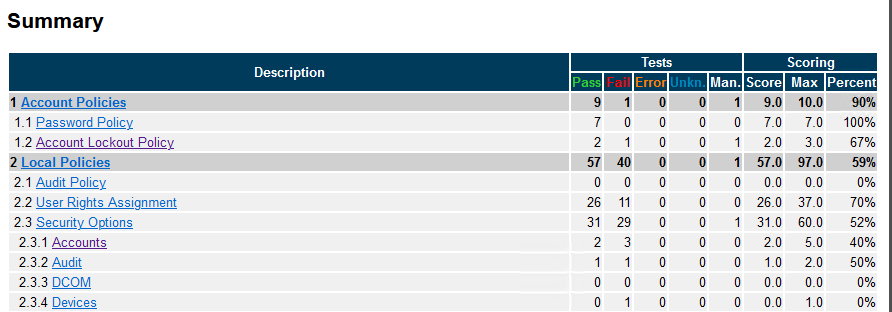
After the assessment completes, navigate back to the CIS-CAT folder and open the “reports” folder. Find the newly minted HTML report in the reports folder for your review.
That is a lot of Red!
If this is your first time running an OS Hardening assessment tool like CIS-CAT, don’t be surprised by all the failures.
False Positives & Ambiguous Value
Not all the results in this test will accurately reflect your security posture, and many of these tests look for things that bring minimal security value. For example, take the following failed test result.
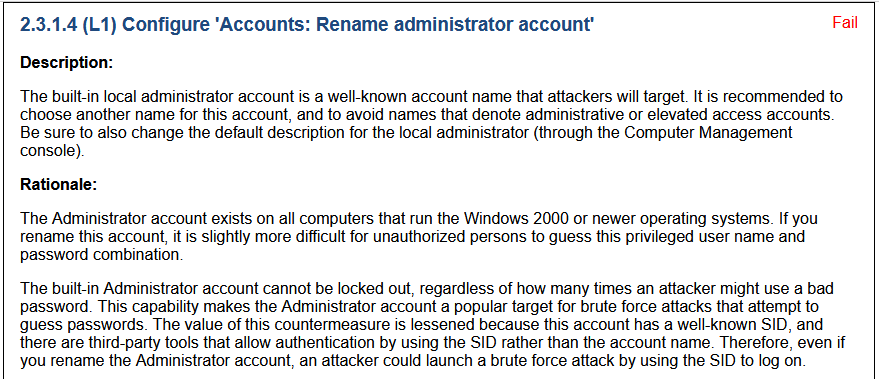
In my case. the Administrator account is disabled, but the test does not consider this. Moreover, the test’s explanation even states renaming the Administrator account brings minimal to no value to security. So just like vulnerability scans that report critical CVS scores of 10 risks, you need to perform your own risk analysis to determine the actual impact.
Fixing Discovered Security Weaknesses
Now that we have a list of security hardening recommendations let’s look at how to fix a failed test result for all systems within our organization. Review the below list of security improvements we need to make.
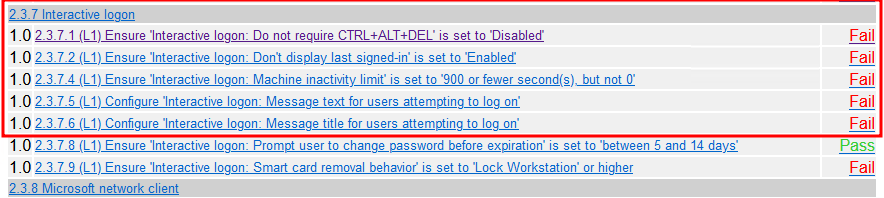
We can click on each test name line, and the link will jump us to the part of the report that explains the test and how to pass it. We can use this information to build a new Active Directory Group Policy Object, which can be applied to mitigate these weaknesses across the whole domain.
Click on the first test name line “Ensure ‘Interactive logon: Do not require CTRL+ALT+DEL’ is set to ‘Disabled’” to review the guidance.
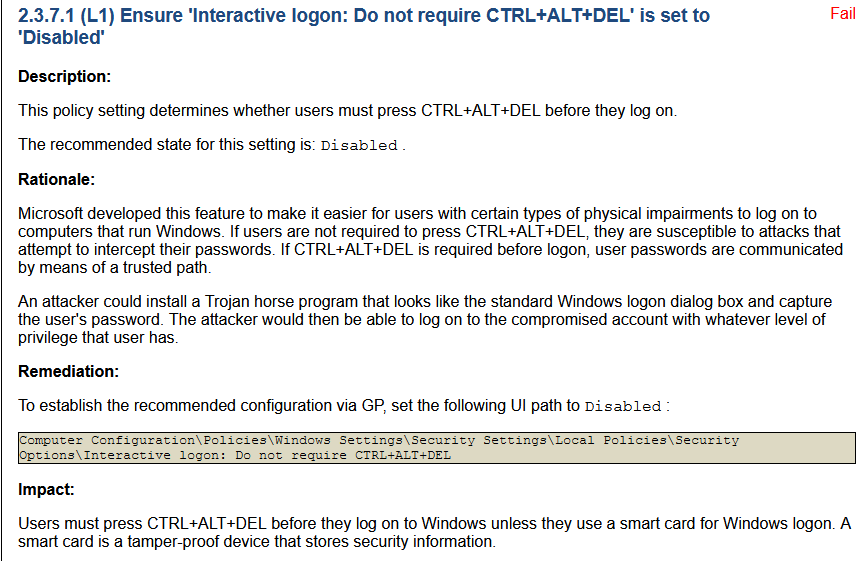
The recommendation looks pretty straightforward and low impact to users. Let’s go to our Active Directory server and create a new GPO called “Local System Interactive Login Control“. We will create one GPO to deploy all the recommendations I highlighted above.
See the screenshot below, where I define the five GPO settings to complete the five CIS-CAT recommendations.
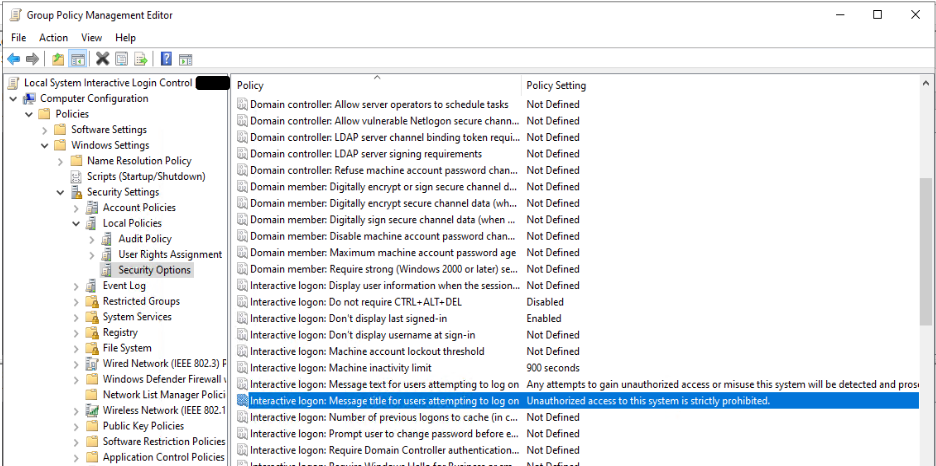
By creating a GPO for our Client systems, we can override the weaker local policy settings for servers and clients. See this TechNet article for a refresher on Group Policy processing and precedence.
Interactive Login Message
I put ChatGPT to good use and had it devise a malicious use deterrent message for my above GPO settings. The message was pretty good, so I thought I would share it with you.
Interactive Login Message Title: ” Unauthorized access to this system is strictly prohibited.“
Interactive Login Message Message: “Any attempts to gain unauthorized access or misuse this system will be detected and prosecuted to the fullest extent of the law. By logging in, you agree to comply with all applicable laws and regulations. Your IP address, login details, and activities on this system will be monitored and recorded. If you are not authorized to use this system, please disconnect immediately and contact the system administrator for further assistance.“
TLDR; Client System Hardening Best Practices & Testing
If you are starting to harden Windows 10/11 client OSs in your environment, use the CIS Benchmark guidance. To test your client OS security hardening policies, do the following.
- Download the CIS-CAT tool and run it on a domain-joined client system.
- Review the report for recommendations and evaluate which ones will bring value.
- Implement the CIS-CAT report recommendations via a GPO in Active Directory to improve security throughout the organization.
That is it! Everything you need to know to implement CIS-CAT report recommendations is contained in the report. If you plan on using CIS Controls throughout your environment, including Windows and Linux servers, I suggest you sign up for the free CIS Workbench site. CIS Workbench is a web portal to access all the CIS documentation and community threads.











Leave a Reply