If you are here, you are either considering taking on Hack The Box’s Dante Pro Lab challenge, or you are stuck and looking for help. Either way, I think you will find some value in this post. There are no spoilers or walkthroughs here, only general advice around completing the Dante Pro Lab. Along with some advice, I will share some of my experiences completing the challenge.
Short on time? TLDR
Dante’s Aging Problem

Dante was once a much harder lab to complete, but due to OS aging, it is much easier now. The Windows servers are all 2012R2 and unpatched. So pwning the box through one of the many new vulnerabilities moves the difficulting from intermediate to easy.
Due to the OS age, most complex challenges -are entirely subverted. One particular system comes to mind that illustrates this issue. After gaining user-level access to the box and deploying a Meterpreter shell, I ran Meterpreter’s “getsystem” command and got full system rights immediately. Upon further enumeration of the server, I discovered an odd binary. Reviewing the binary and considering the metagame of the challenge, I realized that I was supposed to get system-user by reverse-engineering the binary. Instead, what should have taken hours took only a few seconds due to the numerous newer simple-to-exploit OS vulnerabilities.
The OS aging issue applies to the Linux servers as well. Nearly all the Linux boxes are vulnerable to the polkit exploit CVE-2021-3560. I leaned heavily on a tool called Traitor to exploit this newer unpatched Linux vulnerability. So the only real challenge on most systems was getting the initial foothold on the box.
Tunnels in Tunnels in Tunnels

Dante forces you to master building network tunnels. Nearly every system requires at least one tunnel to communicate with it, and others require multiple tunnels layered through the first tunnel. You must combine various network tunneling tools and methods to make the necessary network connections. Some network tunneling tools are good for one tunneling method but bad for others. The discrepancies between each tool’s strengths and weaknesses become apparent when you start having to pass one tunnel through another tunnel. For example, a Meterpreter forwarding tunnel routing through a Chisel reverse tunnel will have a lot of lag time and is unstable.
This tunneling process to reach a system can get confusing. To illustrate, review the networking tunneling diagram below.
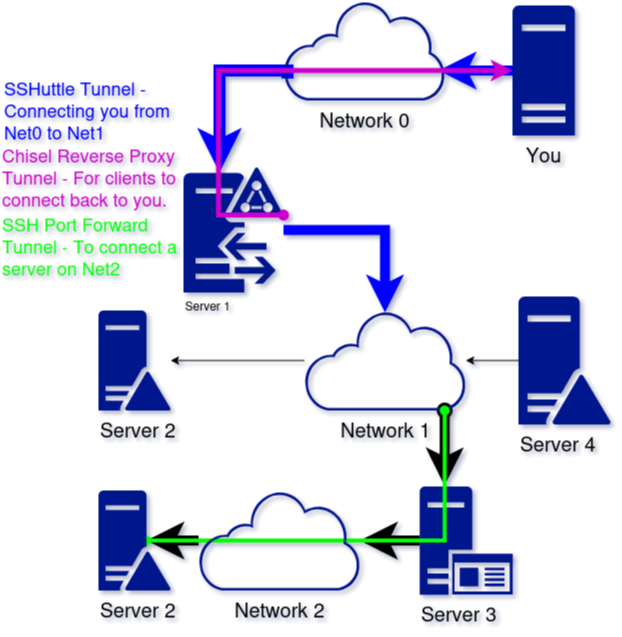
Drawing a simple network diagram of how I would reach a server helped me keep all the connections straight in my head. I recommend you do the same and use a tool like Draw.IO or Visio. In many cases, building the network tunnels to connect to a server will take longer than getting a foothold.
I have two other blog posts to help you understand the tools you need to know to build these networking tunnels.
HTB Dante Skills: Network Tunneling Part 1
HTB Dante Skills: Network Tunneling Part 2
Find & Learn Tools That Will Save Time
Manually enumerating a system after gaining a foothold on any box takes forever. This is why you should learn and use a few helpful tools to speed this process up.

Use WinPEAS to find a path to admin rights on the Windows servers and LinEnum for Linux systems. Use these tools to gather the baseline data for the system, but always manually enumerate after running the script. This lab has many vital pieces of data hidden on the servers, and that data is what you need to progress through the lab.
The Dante Pro Lab is also great for practicing new tools and techniques. I learned the Empire+StarKiller C2 framework during this lab to expedite many processes. Empire proved to be very helpful with system enumerating and documenting. I forgot a few times throughout the lab to document script output or other details, but Empire saved all the script output history. I am not saying you need to use Empire specifically, but rather that you find tools to save time on a real pentest and practice them in this lab.
Wrapping Up Dante Pro Lab – TLDR
Hack The Box’s Pro Lab Dante is a great challenge and will force you to master a few Red Team skills. Before taking on this Pro Lab, I recommend you have six months to a year of experience in Hack The Box. Additionally, If you have only been able to penetrate systems using a guide or walkthrough, you are not ready for this lab.
If you think you are ready for the lab, here are some general tips.
- This lab comprises older OSs, so many “shortcuts” are now open to you. So the Dante Pro Lab is now less complex.
- Expect to do a lot of tunneling. So much tunneling that you will need to draw it all out to keep it clear in your head.
- There is always a path forward. If you are stuck, look at your WinPEAS or LinEnum output again. You likely missed something. If you are still stuck, go back and check the other systems you have already pwned; there may be data you missed.
- Document everything! I make a full copy of the “C:\Users”, “/root” or “/home” after owning a box. This saves me a ton of time later.
Overall I had a great time in this lab and learned a ton. The Dante Pro Lab is great for getting into Pro Labs. Plus, you will have another certificate to add to your resume upon completion!